
Portuguese cybersecurity firm, Naoris Protocol, is fast-tracking the development of the first-ever decentralized cybersecurity infrastructure following a successful funding round. The lead investors in the project include Bitcoin whale Tim Draper, BPMT, Holdun Family Office, SDC Management, and The HOLT Xchange. This latest round brings the cumulative fund raised by Naoris to $31 million.
A Practical Solution
Cybersecurity threats remain prevalent in Web2 infrastructure, and the risks are arguably worsening. Additionally, the increasing adoption of blockchain and other Web3 technologies creates new exposures and vulnerabilities that threat actors could exploit. Consequently, the cost of damages arising from these attacks could surge to an estimated $10 trillion by 2025.
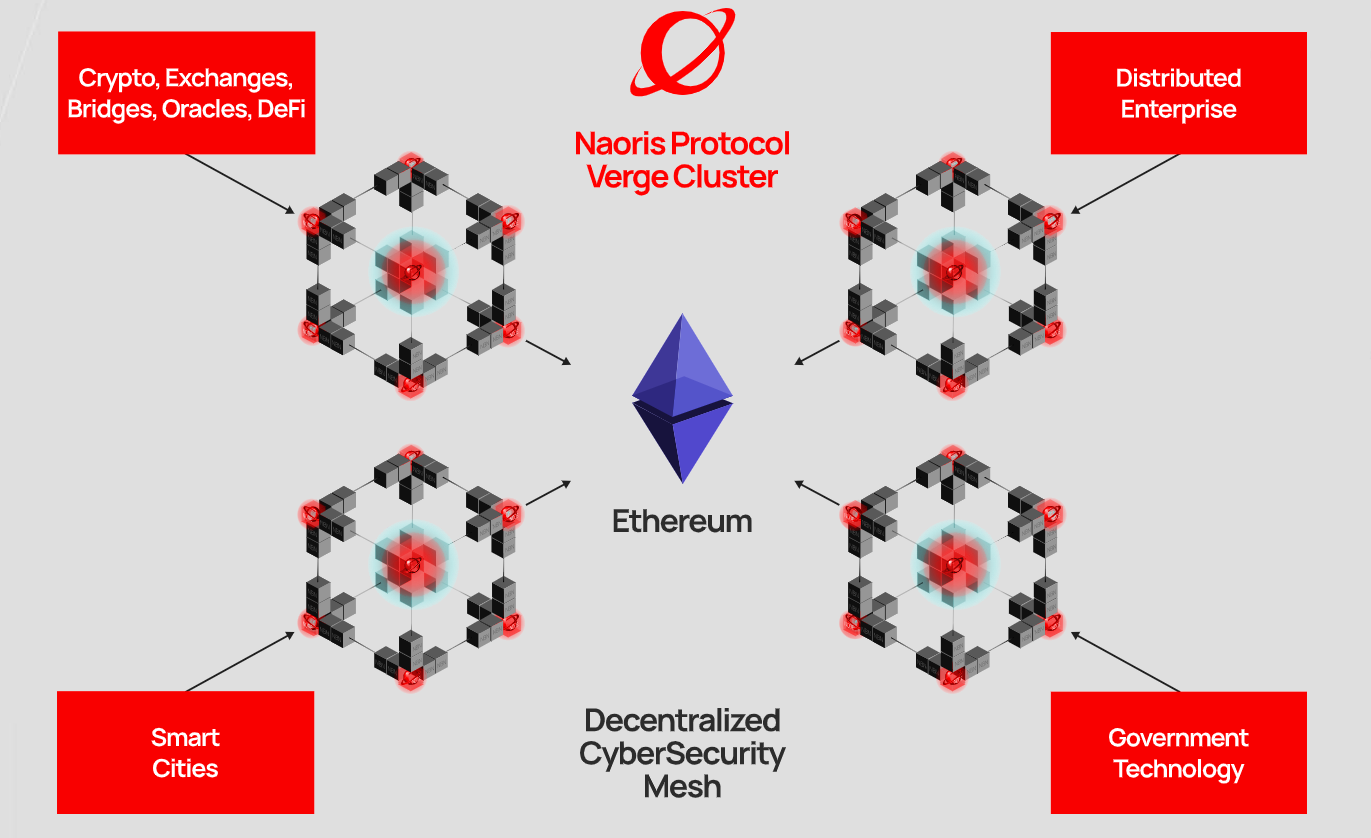
Naoris Protocol aims to seal these gaping security holes through its revolutionary cybersecurity infrastructure – the Decentralized CyberSecurity Mesh. This mesh deploys the decentralized Proof-of-Security (dPoSec) consensus mechanism to secure nodes on the network. Unlike the conventional cybersecurity infrastructure, which is heavily centralized, Naoris Protocol’s mesh distributes network security to eliminate a single point of failure.
Threat actors commonly deploy attacks by exploiting isolated points of failure. For instance, a hacker may send a phishing email or malware to an employee at your organization, who could end up granting the hacker access to your internal systems.
CyberSecurity Mesh powers a network security integrated with all network nodes. So, hackers have to breach all computers in the network before they can access your internal system. Naoris’ cybersecurity infrastructure offers strength in numbers – more nodes in the network make it even harder to execute a breach into the system.
Security that Scales
Although blockchain is relatively new compared to Web2 technologies, the sector has become a preferred target by cyber attackers. These hackers have made away with billions of dollars worth of cryptocurrencies every year. Equally, attacks on Web2 technology aren’t slowing down.
Naoris Protocol leverages blockchain technology to develop a decentralized cybersecurity system. This infrastructure is a game-changer, quite literally. Instead of finding and exploiting vulnerabilities on isolated points of failure, the hackers will have to sweat through their efforts trying to beat an integrated network security system with distributed security gateways.
The decentralized cybersecurity protocol is developed on the Ethereum blockchain and is compatible with the Ethereum Virtual Machine (EVM). This way, the protocol leverages the high scalability of its underlying blockchain, enabling high transaction and process throughput of up to 1 million per second.
In stark contrast with the conventional cybersecurity solutions that quickly reach capacity, Naoris Protocol’s mesh distributes critical security operations across the network. So the protocol is scalable and operates optimally.
Breaches to traditional network security systems often via the weakest link in the chain, but with Naoris, the decentralized mesh ensures all cybersecurity links are robust and can not compromise the whole chain. The protocol’s dPoSec consensus mechanism powers this distributed security system.
Neutral and Permissionless
Centralized cybersecurity solutions run the risk of bias or censorship. This way, your network may fall victim to targeted malicious attacks due to censorship or bias by your security provider. A decentralized cybersecurity framework eliminates the need for a central governing authority, promoting neutrality and permissionless governance. This feature makes the protocol especially important for organizations that serve public interests, like governments.
Naoris Protocol runs Verge Clusters, which are similar to sub-chains of Ethereum. Each cluster supports unique security operations. This expansive network of clusters allows for more processes to run on the decentralized cybersecurity mesh making it even harder for a possible attack or breach.
Reward-based Protocol
The protocol developed will suffice for both Web2 and Web3 cybersecurity problems. As new nodes join the network, existing nodes will participate in validating the new devices. This process will earn the validator $CYBER tokens – the protocol’s native token. The reward system incentivizes more users to take up Naoris Protocol and validators to keep the network secure from malicious nodes. This incentive powers the permissionless governance of the protocol. The $CYBER token has additional utility, including staking and transfer of value.
Use Cases
Blockchain technology has been the missing link for cybersecurity solutions. Leveraging EVMs for Naoris offers distributed security eliminating central points of failure that are otherwise easy threat targets. With this protocol, institutions can secure critical infrastructure and other government technology.
Web3 platforms like exchanges, bridges, DeFi projects, and oracles should adopt this decentralized network security solution to protect their critical infrastructure.
A Bright Future
All investors in the latest round of funding have expressed high approval for Naoris Protocol. Citing the project’s high utility across various Web2 and Web3 applications, the investors show confidence in high user adoption. With this funding, Naoris is accelerating its dPoSec and decentralized CyberSecurity Mesh development.
The project’s CEO David Carvalho aims to have the dPoSec up and running by the end of 2022 as Naoris Protocol scales. The protocol aims to create a ready-to-use interface attracting new users and those shifting to Web3. The protocol security features do not interfere with Layer 1 and Layer 2 solutions.
Will this be the solution to make cyber threats a thing of the past?
Learn More
To get started with the Naoris Protocol, explore the whitepaper here. Also, stay up-to-date with the latest from Naoris by connecting to their socials on Twitter, Discord, and Telegram.













